4 Simple Ways To Protect Yourself From Cyberattacks

It’s Cybersecurity Awareness Month and it’s the perfect time to share information on simple necessary actions required to protect yourself and devices from cyberattacks. The majority of internet savvy Nigerians have been victims of cyberattacks or know at least one person who has. Cybercriminals have consistently deployed several attack strategies to rip people off their money. There have been reports of phone hacks where the attackers make requests from loan applications, thereby plunging the victim into huge financial debts. Others go as far as reaching out to the victim’s contacts with distressing messages, whipping up emotional scenarios, all in a bid to steal from them.
According to the Nigerian Communications Commission (NCC), the country loses about $500m annually to cybercrime. So, there’s need for adequate protection of your online activities. Following the simple tips makes you one step ahead.
1. Always Use Strong Passwords and Enable Multi-Factor Authentication (MFA)
Secure your accounts and online presence with strong, unique passwords for every account. Avoid using the same password for all your accounts, as one successful unauthorised login attempt leaves your other accounts vulnerable.
In addition to strong passwords, enable multi-factor authentication (MFA) to provide another layer of protection, making it much harder for attackers to access your accounts.
Here are some simple tips when creating a password
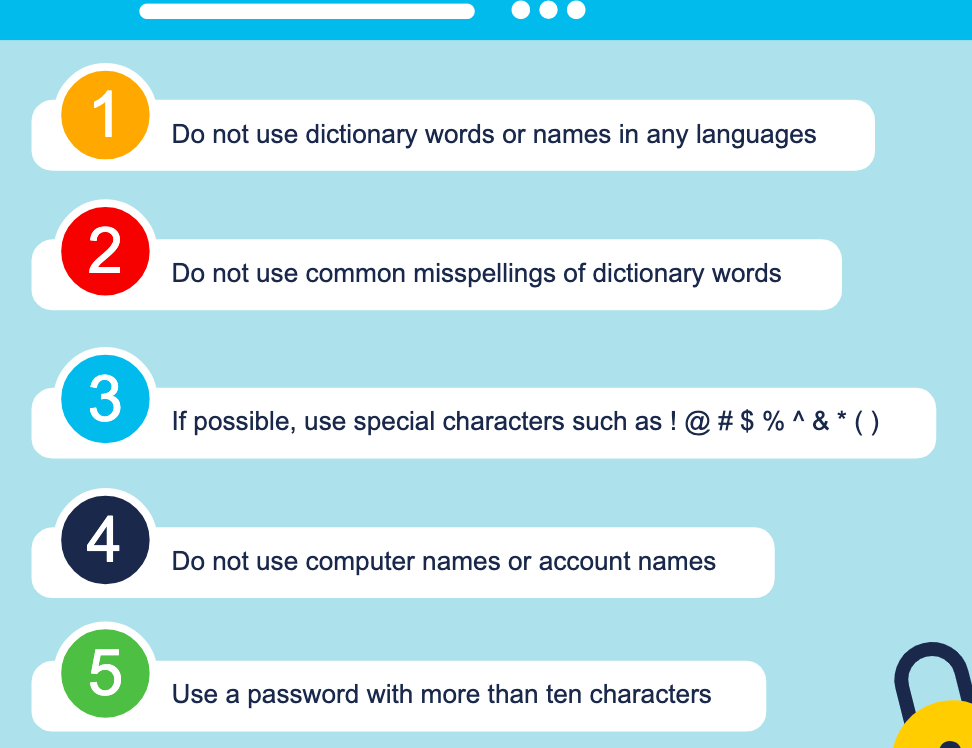
2. Use a passphrase
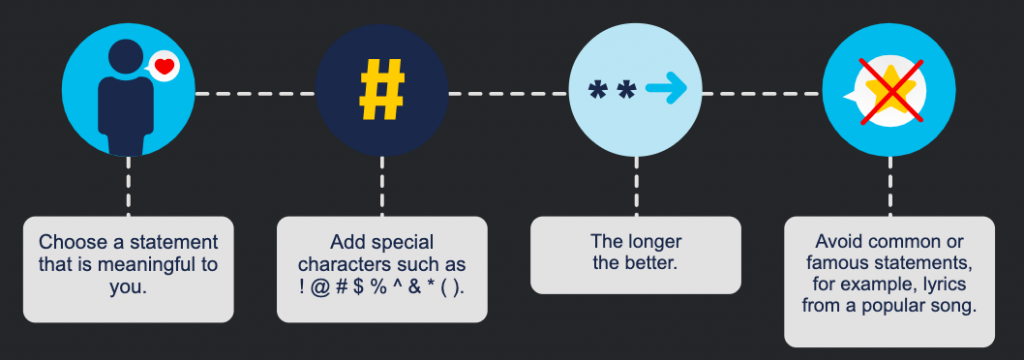
Another smart way to prevent unauthorised access to your devices, is to use passphrases instead of passwords. A passphrase generally takes the form of a sentence (‘Aboyth@tlov3sc@ts.’), making it easier for you to remember. Its length makes you less vulnerable to attacks.
3. Be Careful of Suspicious Communications
Before clicking that link or downloading that file, take a step back and make some findings. Send a direct email to the company’s email because hackers use cloning techniques, making it difficult for you to differentiate between what’s real or not. For example, you received an email from “AppIe,” but the hacker used capitalised “I” instead of “l”. Also, any communication requesting sensitive personal information is a red flag.
4. Update Your Devices and Softwares
Software and device updates can sometimes be clunky and difficult to navigate, especially when there are many changes; however, installing them promptly protects you from attacks, as they usually fix security vulnerabilities.